- Power BI forums
- Updates
- News & Announcements
- Get Help with Power BI
- Desktop
- Service
- Report Server
- Power Query
- Mobile Apps
- Developer
- DAX Commands and Tips
- Custom Visuals Development Discussion
- Health and Life Sciences
- Power BI Spanish forums
- Translated Spanish Desktop
- Power Platform Integration - Better Together!
- Power Platform Integrations (Read-only)
- Power Platform and Dynamics 365 Integrations (Read-only)
- Training and Consulting
- Instructor Led Training
- Dashboard in a Day for Women, by Women
- Galleries
- Community Connections & How-To Videos
- COVID-19 Data Stories Gallery
- Themes Gallery
- Data Stories Gallery
- R Script Showcase
- Webinars and Video Gallery
- Quick Measures Gallery
- 2021 MSBizAppsSummit Gallery
- 2020 MSBizAppsSummit Gallery
- 2019 MSBizAppsSummit Gallery
- Events
- Ideas
- Custom Visuals Ideas
- Issues
- Issues
- Events
- Upcoming Events
- Community Blog
- Power BI Community Blog
- Custom Visuals Community Blog
- Community Support
- Community Accounts & Registration
- Using the Community
- Community Feedback
Earn a 50% discount on the DP-600 certification exam by completing the Fabric 30 Days to Learn It challenge.
- Power BI forums
- Forums
- Get Help with Power BI
- Desktop
- Re: Power BI REST API using Service Principal
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Power BI REST API using Service Principal
Hi,
I'm trying to use a Power BI REST API to retrieve info about one of our workspaces. To do this, it's crucial we make use of a Service Principal.
So far I've used a POST request in Postman to retrieve the bearer token. To do this I've used the 4 parameters I've seen specified in documentation/other tickets, which are: grant_type, client_id, client_secret, scope.
This then outputs a bearer token, which gives me confidence that we've set up the Service Principal correctly and that it's working as it should be: so far so good.
However when I attempt to use this bearer token as an input for a GET request e.g. where I'm looking to return workspaces in our tenant, it comes back with 401 unauthorized.
Initially I thought I may not be calling the endpoint correctly, so tested it in Postman using a bearer token I produced while working in the MS sandbox that accompanies the documentation online. This returned the workspaces I'm seeking, but of course doesn't use the Service Principal.
My question is - should a simple cut and paste of the bearer token that's output from the POST request, into the Authorization section (Bearer Token) of the GET request not output the workspaces I'm after?
Could really do with some help on this as we've been going in circles for a while!
Thank you,
Shane
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @SG_synapx ,
Thanks for reaching out to us with your problem. The 401 unauthorized error typically indicates that you didn't have the sufficient privilege to access the resource. In order to make further troubleshooting and give you a suitable solution, could you please provide the following info? It would be helpful to find the solution. Thank you.
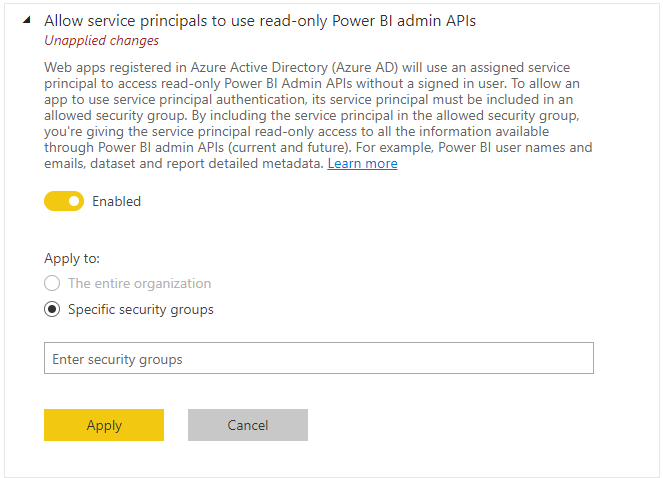
- Tenant settings: Make sure "Allow service principals to use read-only Power BI admin APIs" is enabled.
- Workspace access: Add the service principal(the Display Name of the Azure AD app) as the admin of workspace. If service principal is in security group, please also add this service principal as the admin of workspace.
powerbi - Unauthorized (401) Power BI Embedded using the samples Node and .NET - Stack Overflow
- Check Token Acquisition: Verify that the 'scope' parameter in your POST request is set correctly. For Power BI, it should be 'https://graph.microsoft.com/.default'. - Ensure that the 'grant_type' is set to 'client_credentials'.
- Use the Token Correctly: When you paste the bearer token into the Authorization section of the GET request, ensure that there are no leading or trailing spaces. - Confirm that the token has not expired. Tokens typically have a 1-hour lifespan.
- Test the API Call: Use the same GET request that worked in the MS sandbox, but replace the bearer token with the one obtained through the Service Principal.
In addtion, the following ones are the threads which has the similar problem as yours. Hope they can help you.
Solved: Power Bi REST API - 401 Authorization error when u... - Microsoft Fabric Community
Solved: Power Bi REST API - 401 Authorization error when u... - Microsoft Fabric Community
Best Regards
If this post helps, then please consider Accept it as the solution to help the other members find it more quickly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi v-yiruan-msft ,
Thanks for getting back to me.
I'll run through your suggestion points one-by-one:
• Tenant settings - The service principal has been given all the necessary permissions by the admin in Azure
• Workspace access - This has caused us a little confusion as the GET request we're dealing with operates on a tenant-level, bringing back all workspaces. Would we still need to give the service principal admin access to every workspace? Seems like overkill..
• Token acquisition - I was initially using a different URL for the scope parameter, 'https://analysis.windows.net/powerbi/api/.default'. Changing this to the URL you've suggested has made a difference, so I'll go into more detail below
• Using the token correctly - I can confirm that this wouldn't be the cause of our issue, we were quite diligent on this point
• Testing the API call - The GET request we've been calling is to return the workspaces in our tenant, and I can confirm this works fine in MS sandbox, and also in Sandman where we used the same bearer token produced in MS sandbox as a test, so no problems there.
Note:
The only aspect I've changed is updating the URL for the scope parameter, along the lines of what you've suggested. This has brought back a 403 Forbidden error as opposed to the 401 Authorization error from before. I've researched the error and tried a few different params but can't am still coming back with 403s.
If there's something more I should be doing please let me know!
Thanks for your help,
Shane
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I’m having exactly the same problem. I’m already going crazy!
It work only user functions, but when i use an admin function, i got the 401 error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I resolved!
I leave just the permission Tenant.ReadWrite.All (Type delegated) on power bi service and remove all the others.
Also on admin portal power bi, i allowed app embed to my security group. Now, its working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you willing to share your Postman collection with me? Because I am getting stuck everytime connecting through Service Principal, drives me crazy.
Helpful resources
| User | Count |
|---|---|
| 98 | |
| 90 | |
| 77 | |
| 71 | |
| 64 |
| User | Count |
|---|---|
| 114 | |
| 98 | |
| 96 | |
| 68 | |
| 67 |