- Power BI forums
- Updates
- News & Announcements
- Get Help with Power BI
- Desktop
- Service
- Report Server
- Power Query
- Mobile Apps
- Developer
- DAX Commands and Tips
- Custom Visuals Development Discussion
- Health and Life Sciences
- Power BI Spanish forums
- Translated Spanish Desktop
- Power Platform Integration - Better Together!
- Power Platform Integrations (Read-only)
- Power Platform and Dynamics 365 Integrations (Read-only)
- Training and Consulting
- Instructor Led Training
- Dashboard in a Day for Women, by Women
- Galleries
- Community Connections & How-To Videos
- COVID-19 Data Stories Gallery
- Themes Gallery
- Data Stories Gallery
- R Script Showcase
- Webinars and Video Gallery
- Quick Measures Gallery
- 2021 MSBizAppsSummit Gallery
- 2020 MSBizAppsSummit Gallery
- 2019 MSBizAppsSummit Gallery
- Events
- Ideas
- Custom Visuals Ideas
- Issues
- Issues
- Events
- Upcoming Events
- Community Blog
- Power BI Community Blog
- Custom Visuals Community Blog
- Community Support
- Community Accounts & Registration
- Using the Community
- Community Feedback
Register now to learn Fabric in free live sessions led by the best Microsoft experts. From Apr 16 to May 9, in English and Spanish.
- Power BI forums
- Issues
- Issues
- BUG : Power BI is not executing the Roles of the M...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
BUG : Power BI is not executing the Roles of the Multidimensional Roles when using Direct connection
BUG : Power BI service is not executing the Roles of the Multidimensional Roles when using Direct connection via the Gateway.
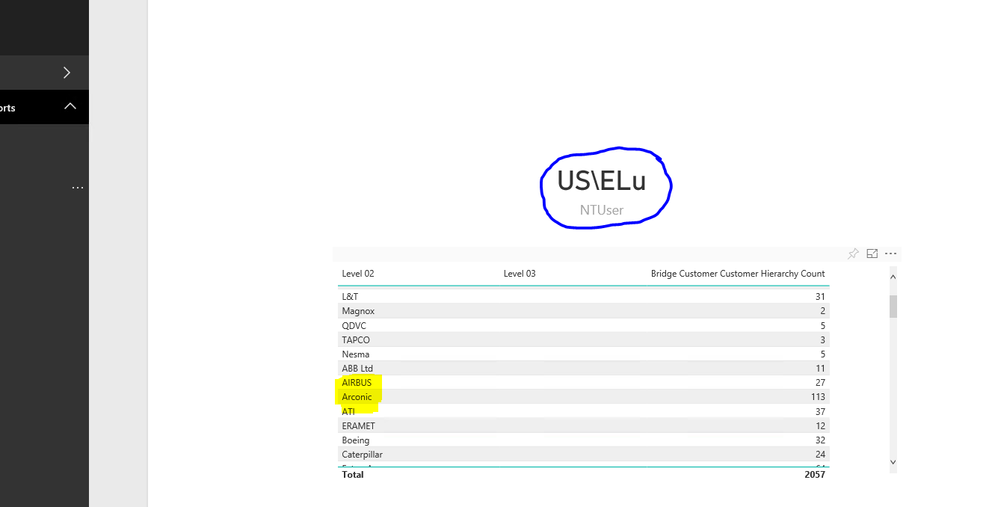
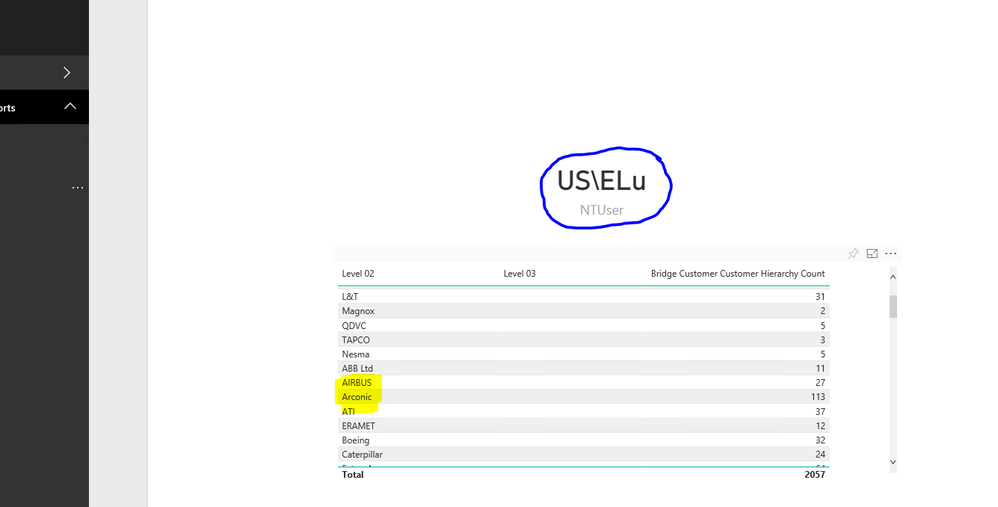
The Power BI gateway is successfully set and the effective user name has identified the user connecting and the replacement of this with the Active Directory is working . As the report is showing the User name e.g "US\Elu". See highlighted in blue line.
This is a Power BI Gateway communicating to an on premise gateway communicating with Direct connect to the Analysis Services multidimensional cube. The server administrator is successfully connecting and as mentioned effective user name is passing the users AD account details through to Analysis services.
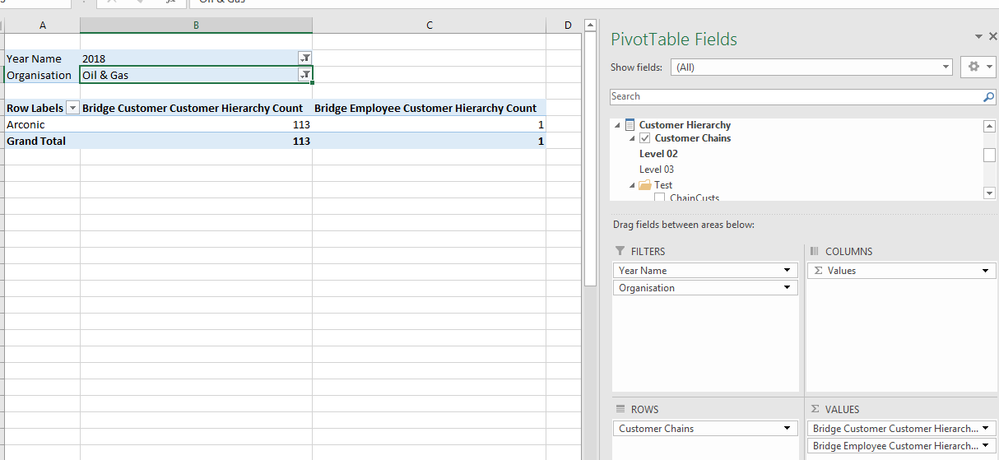
The dynamic role is correctly filtering the customers to those authorised for the user when the user connects via Excel, In this case the list is limited to "Acronis"
However Power Bi is not executing the roles correctly as the report is returning all the customer and not the authorised one,e.g Acronis. See Acronis and Airbus in yellow as well as all the other customers.
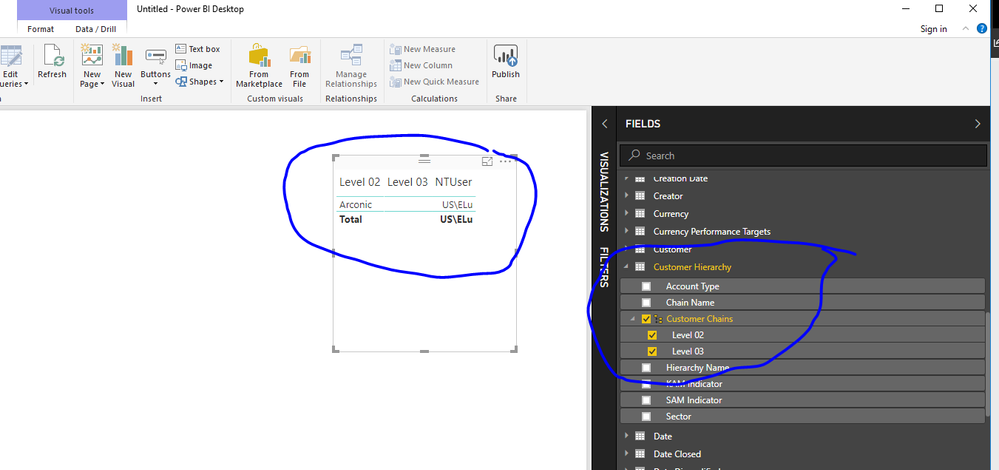
Finally when I build a report in Power BI desktop and log in as US\Elu the report using direct connnect does respect the SSAS cubes role as it only returns the authorised customer "Acronis". So the code in the role is valid and works! As you can see below circled by a blue line.
Please answer why the power BI service is not executing the roles when the report is run.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- spindive on: Possible Bug with Rounding
-
 v-xiaoyan-msft
on:
export to excel
v-xiaoyan-msft
on:
export to excel
-
 v-xiaoyan-msft
on:
Is there any way to see the full name of the colum...
v-xiaoyan-msft
on:
Is there any way to see the full name of the colum...
-
 v-xiaoyan-msft
on:
Issue with Client Credentials Grant Type for Power...
v-xiaoyan-msft
on:
Issue with Client Credentials Grant Type for Power...
- MattSwan on: Multi-Select Possible in Filter Panel even when Re...
-
 v-xiaoyan-msft
on:
TypeConversionFailure when not trying to convert
v-xiaoyan-msft
on:
TypeConversionFailure when not trying to convert
-
 Idrissshatila
on:
Power Query Filter Rows Basic UI bug
Idrissshatila
on:
Power Query Filter Rows Basic UI bug
-
 v-yetao1-msft
on:
Wrong french translation for "reader" permission
v-yetao1-msft
on:
Wrong french translation for "reader" permission
-
 v-yetao1-msft
on:
'Select All' option in a slicer is not intuitive w...
v-yetao1-msft
on:
'Select All' option in a slicer is not intuitive w...
- MurtoMan on: Bug in quick filter in PBI Desktop
- New 7,844
- Needs Info 3,356
- Investigating 3,134
- Accepted 2,036
- Declined 38
- Delivered 3,747
-
Reports
9,669 -
Dashboards
3,902 -
Data Modeling
3,856 -
Gateways
2,042 -
Report Server
2,001 -
APIS and Embedding
1,884 -
Custom Visuals
1,670 -
Content Packs
502 -
Mobile
347 -
Need Help
11 -
Show and Tell
2 -
General Comment
2 -
Tips and Tricks
1 -
Power BI Desktop
1