- Power BI forums
- Updates
- News & Announcements
- Get Help with Power BI
- Desktop
- Service
- Report Server
- Power Query
- Mobile Apps
- Developer
- DAX Commands and Tips
- Custom Visuals Development Discussion
- Health and Life Sciences
- Power BI Spanish forums
- Translated Spanish Desktop
- Power Platform Integration - Better Together!
- Power Platform Integrations (Read-only)
- Power Platform and Dynamics 365 Integrations (Read-only)
- Training and Consulting
- Instructor Led Training
- Dashboard in a Day for Women, by Women
- Galleries
- Community Connections & How-To Videos
- COVID-19 Data Stories Gallery
- Themes Gallery
- Data Stories Gallery
- R Script Showcase
- Webinars and Video Gallery
- Quick Measures Gallery
- 2021 MSBizAppsSummit Gallery
- 2020 MSBizAppsSummit Gallery
- 2019 MSBizAppsSummit Gallery
- Events
- Ideas
- Custom Visuals Ideas
- Issues
- Issues
- Events
- Upcoming Events
- Community Blog
- Power BI Community Blog
- Custom Visuals Community Blog
- Community Support
- Community Accounts & Registration
- Using the Community
- Community Feedback
Register now to learn Fabric in free live sessions led by the best Microsoft experts. From Apr 16 to May 9, in English and Spanish.
- Power BI forums
- Forums
- Get Help with Power BI
- Developer
- Re: PowerBI Admin Rest API - Azure app registratio...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
PowerBI Admin Rest API - Azure app registration - dont know how to connect from Postman
We are trying to build a database with PowerBI auditing information.
In our case, the ideal solution is, that we want to load data from the REST APIs towards AWS. (I know.. don't ask... 🙂
We have setup an Azure AD App registration for this. Inspired by several youtube videos and this blog post:
How to Call the Power BI REST API from Postman - Carl de Souza
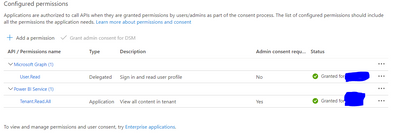
For this app, we have requested our office tenant admin to approve Tenant.Read.All privileges.
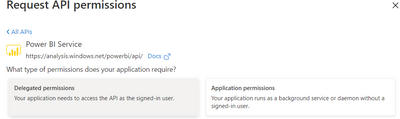
That is probably a little different than what Carl described. I dont want to use the "delegated permissions" since I dont want to logon with my corporate ID, but I want to login with a clientID and secret coming from our AWS environment.
My issue is now, that I am trying to connect from Postman, but I am failing.
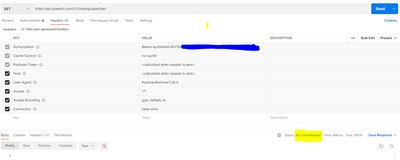
First I am trying to do a Post to get a bearer token. This seems succesful, although I am wondering: should I also see a "scope" mentioned in the result? I have seen it with other screenshots on the web.
Then, while trying to do a simple get, using this bearer token, I am getting a "401 unauthorized".
Can someone please suggest what I am doing wrong? Any suggestion would be highly appreciated!
Update:
meanwhile I came across this article about Service Principals
Enable service principal authentication for read-only admin APIs - Power BI | Microsoft Docs
Would that be the right way to go? I tried some of the steps, and went to a different error message:
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@vandenhende , the link is the right way to do it. You need to:
1. Create the security group
2. Add the service principal in a security group.
3. Enable the "Allow service principals to use read only ..." feature
4. Add the security group in "Allow service principals to use read only ..."
Re-test after 10-15 minutes (AAD groups and member propagation in all services)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@vandenhende , the link is the right way to do it. You need to:
1. Create the security group
2. Add the service principal in a security group.
3. Enable the "Allow service principals to use read only ..." feature
4. Add the security group in "Allow service principals to use read only ..."
Re-test after 10-15 minutes (AAD groups and member propagation in all services)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed! I just figured out that this works!
It took quite some time to learn that this was the right approach.
Thanks for your support!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I maybe won't help to much with this but, for the app that we have, we need to invite the user as a guest to the tenant and add him to the security group on the Azure ad, then that group need to be part of the app access. When you create any app on Azure, you also have enterprise applications and under your app, you need to add that group otherwise, they won't be able to access it.
Helpful resources

Microsoft Fabric Learn Together
Covering the world! 9:00-10:30 AM Sydney, 4:00-5:30 PM CET (Paris/Berlin), 7:00-8:30 PM Mexico City

Power BI Monthly Update - April 2024
Check out the April 2024 Power BI update to learn about new features.

| User | Count |
|---|---|
| 12 | |
| 2 | |
| 2 | |
| 1 | |
| 1 |